IndiMail 1.7.3 comes with option in svctool to install QMQP service.
IndiMail 1.7.5 will come with RPM package indimail-mini which will allow you to install a mini indimail installation. A mini indimail installation comes up with a bare minimum list of programs to enable you to send out mails. A indimail-mini installation doesn't have a mail queue. Instead it gives each new message to a central server through QMQP.
Many of my friends run web servers which need to send out emails. If you already have an installation of
IndiMail messaging server on your network, you can quickly setup a mini indimail installation on your web server, without impacting the performance by using QMQP. To use QMQP service, you need to have QMQP service running on your IndiMail messaging server. All other servers (including your webservers) can have a indimail-mini installation.
How do I set up a QMQP service?
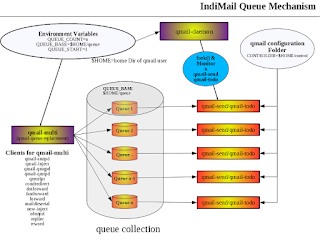
You need to have at least one host on your network offering QMQP service to your clients. IndiMail includes a QMQP server, qmail-qmqpd. Here's how to set up QMQP service to authorized client hosts on your IndiMail messaging server.
first create /var/indimail/etc/tcp.qmqp in tcprules format to allow queueing from the authorized hosts. make sure to deny connections from unauthorized hosts. for example, if queueing is allowed from 1.2.3.*:
1.2.3.:allow
:deny
Then create /var/indimail/etc/tcp.qmqp.cdb:
% sudo /var/indimail/bin/tcprules /var/indimail/etc/tcp.qmqp.cdb \
/var/indimail/etc/qmqp.tmp < /var/indimail/etc/tcp.qmqp
You can change /var/indimail/etc/tcp.qmqp and run tcprules again at any time. Finally qmail-qmqpd to be run under supervise:
% sudo /var/indimail/sbin/svctool --qmqp=628 --servicedir=/service \
--qbase=/var/indimail/queue --qcount=5 --qstart=1 \
--cntrldir=control --localip=0 \
--maxdaemons=75 --maxperip=25 --fsync --syncdir \
--memory=104857600 --min-free=52428800
628 is the TCP port for QMQP.
How do I install indimail-mini?
A indimail-mini installation is just like a indimail installation, except that it's much easier to set up:
* You don't need MySQL
* You don't need /var/indimail/alias. A indimail-mini installation doesn't do any local delivery.
* You don't need indimail entries in /etc/group or /etc/passwd. indimail-mini runs with the same privileges as the user sending mail; it doesn't have any of its own files.
* You don't need to start anything from your boot scripts. indimail-mini doesn't have a queue, so it doesn't need a long-running queue manager.
* You don't need to add anything to inetd.conf. A null client doesn't receive incoming mail.
Here's what you do need:
* qmail-qmqpc, forward, qmail-inject, sendmail, predate, datemail, mailsubj, qmail-showctl, maildirmake, maildir2mbox, maildirwatch, qail, elq, and pinq in /var/indimail/bin;
* a symbolic link to qmail-qmqpc from /var/indimail/bin/qmail-queue;
* symbolic links to /var/indimail/bin/sendmail from /usr/sbin/sendmail and /usr/lib/sendmail (for Fedora see the topic on /usr/sbin/alternatives below)
* all the manual pages in /var/indimail/man;
You can install all the above by manually copying the binaries and man pages from a host having standard IndiMail installation or you can using the indimail-mini RPM
% sudo rpm -ivh indimail-mini-1.7.5-1.1.i386.rpm
Apart from the binaries, you need to do the following
* a list of IP addresses of QMQP servers, one per line, in /var/indimail/control/qmqpservers;
* a copy of /var/indimail/control/me, /var/indimail/control/defaultdomain, and /var/indimail/control/plusdomain from your central server, so that qmail-inject uses appropriate host names in outgoing mail; and
* this host's name in /var/indimail/control/idhost, so that qmail-inject generates Message-ID without any risk of collision.
Everything can be shared across hosts except for /var/indimail/control/idhost.
Remember that users won't be able to send mail if all the QMQP servers are down. Most sites have two or three independent QMQP servers.
Note that users can still use all the qmail-inject environment variables to control the appearance of their outgoing messages.
Fedora - Using /usr/sbin/alternatives
Sometimes two or more Fedora package exist that serve the same purpose. The
alternatives system provides a mechanism for selecting an active default application from several valid alternatives. You can use the
alternatives system to configure as an alternative MTA for your system. Using alternatives, you don't have to create the links to /var/indimail/bin/sendmail manually as instructed above.
% sudo /usr/sbin/alternatives --install \
/usr/sbin/sendmail mta /var/indimail/bin/sendmail 120 \
--slave /usr/share/man/man8/sendmail.8.gz mta-sendmailman \
/var/indimail/man/man8/qmail-inject.8.gz \
--slave /usr/lib/sendmail mta-sendmail \
/var/indimail/bin/sendmail
/usr/sbin/alternatives --set mta /var/indimail/bin/sendmail
You can download IndiMail at
http://sourceforge.net/projects/indimail/
The RPM can be downloaded from
http://download.opensuse.org/repositories/home:/indimail/
NOTE: This document is based on '
Installing min-qmail' by djb