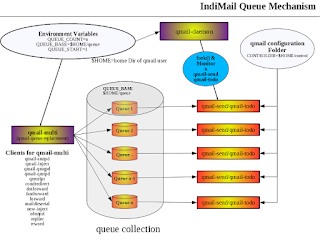
IndiMail 1.6 onwards implements greylisting using qmail-greyd daemon. You additionally need to have the environment variable GREYIP defined for the qmail-smtpd process. The environment variable GREYIP specifies on which IP and port, qmail-greyd is accepting greylisting requests. qmail-smtpd uses UDP to send a triplet (IP+RETURN_PATH+RECIPIENT) to the greylisting server and waits for an answer which tells qmail-smtpd to proceed ahead or to temporarily reject the mail. qmail-greyd also accepts a list of whitelisted IP addresses for which greylisting should not be done.
1. Enabling qmail-greyd greylisting server
% su
# svctool --greylist=1999 --servicedir=/service --min-resend-min=2 \
--resend-win-hr=24 --timeout-days=30 --context-file=greylist.context \
--save-interval=5 --whitelist=greylist.whitelist --use-greydaemon
NOTE: The above service has already been setup for you, if you have done a binary installation of IndiMail/indimail-mta
2. Enabling greylisting in SMTP
- Assuming you've setup your qmail-smtpd service with tcpserver with the
-xoption (as in LWQ), you just need to update the cdb file referenced by this-xoption. The source for this file is typically/etc/indimail/tcp.smtp. For example,127.:allow,RELAYCLIENT=""192.168.:allow,RELAYCLIENT="":allow - could become,127.:allow,RELAYCLIENT=""192.168.:allow,RELAYCLIENT="":allow,GREYIP="127.0.0.1@1999"
- If you've setup
qmail-greydon a non-default address (perhaps you're runningqmail-greydon a separate machine), you'll also need to specify the address it's listening on - adjust the above to includeGREYIP="192.168.5.5@1999", for example. - Finally, don't forget to update the cdb file corresponding to the source file you've just edited. If you have a LWQ setup that's,# qmailctl cdb
- Alternatively (and particularly if you're not using the
-xoption totcpserver) you can enable greylisting for all SMTP connections by settingGREYIPin the environment in whichqmail-smtpdis started - for example your variables directory for qmail-smtpd can contain a file with the name GREYIP# echo GREYIP=\"127.0.0.1@1999\" > /service/qmail-smtpd.25/variables/GREYIP
NOTE: The above instructions are for IndiMail/indimail-mta 2.x and above. For 1.x releases, use /var/indimail/etc for the location of tcp.smtp and tcp.smtp.cdb